BLOG | SERVICE MANAGEMENT
A well-thought-out, scalable, and flexible permission management system is essential for every organization. It ensures security, data protection, and compliance, reduces the complexity of managing roles and responsibilities, and boosts efficiency – allowing all employees to perform their tasks without hindrance.
Building on the challenges of implementation, this article provides helpful strategies and describes the elements required for concrete implementation in OTOBO. Are you wondering if OTOBO meets your requirements for implementing a scalable and future-proof permission management system? Then this article is the perfect starting point for you.
Challenges to Consider When Implementing a Permission Concept
When setting up a permission concept in a service management solution like OTOBO, you’ll face several challenges:
- Organizational Complexity: Small to medium-sized businesses (SMBs) need simple permission concepts that are easy to manage efficiently.
Larger companies with many departments, teams, and roles can make it tough to implement a flexible permission concept, as numerous access rights and restrictions must be considered. The same applies to organizations with decentralized structures – such as those with multiple branches or external partners who require specific access rights. They need finer-grained control over permissions to manage complexity simply and efficiently. Implementing role-based access control (RBAC) models can be particularly beneficial in these cases.
- Dynamic Change: Structures, processes, and associated responsibilities are constantly changing. Your permission concept must adapt quickly to ensure access rights remain up-to-date and employees can work efficiently and productively at all times.
- Scalability: Whether it’s a company-wide rollout or the acquisition and integration of additional business units, your service management solution’s permission management must be able to scale with your organization and growing user base without overwhelming administration.
- Security and Compliance: Ensuring compliance with data protection regulations like GDPR and providing employees with targeted access to the data they need for their daily work is essential. So is preventing unauthorized access to sensitive data.
- Integration with Other Systems: For organizations that have already solved permission management elsewhere, it’s crucial to be able to import permission structures from external systems instead of maintaining them locally in the service management solution. Integration capabilities for dynamically importing permissions from systems like Active Directory, LDAP, or other identity and access management systems are vital.
- Role and Rights Management: A flexible concept enables administrators to create roles and rights dynamically and modify or remove them with minimal effort to meet new requirements. An intuitive and easy-to-maintain permission system ensures they can perform these tasks efficiently.
Strategies for Successful Permission Management
To overcome challenges and implement efficient permission management, organizations can leverage a range of best practices:
- Detailed Role and Rights Analysis: Start with a comprehensive analysis of roles and rights within your organization to ensure all user groups and roles are defined and meet actual needs.
The principle of least privilege avoids over- or under-authorization by granting each user only the rights they need for their tasks. This prevents users from accessing sensitive information or features they don’t need.
- Implementing a Role-Based Access Control (RBAC) Model: An RBAC model allows you to assign access rights based on roles rather than individual users, making permission management easier and more secure. Clearly defining roles and responsibilities within your organization is crucial for implementing an effective permission concept.
- Regular Review and Adjustment: Regularly reviewing your permission concept is essential to ensure it remains up-to-date. This guarantees that changing requirements are reflected and assigned roles and groups have the necessary permissions. Your service management solution should support this step with a clear overview of the current state.
- Adopting Existing Permissions: Manually managing permissions can be error-prone and time-consuming, especially with large user numbers. Importing permissions from centrally managed systems like Active Directory (AD) or LDAP reduces effort and helps avoid inconsistencies and security gaps.
- Security and Compliance Policies: Your organization’s existing security and compliance policies must be considered to ensure the implemented permission concept meets requirements and adheres to relevant regulations.
- Training and Documentation: All administrators and users should be adequately trained to understand and effectively use the permission concept. Detailed documentation of the configuration and permissions helps you quickly get an overview of existing structures in case of changes and avoid problems.
Implementing Permission Management in OTOBO
The key elements for implementing permission management in OTOBO are users, groups, and roles.
Users: Internal and External OTOBO User Groups
OTOBO distinguishes between three user types: Administrators, Agents, and Customer Users.
Administrators have full access to all features and settings in OTOBO.
Agents are the typical users of the OTOBO backend, such as IT service management team members or staff from departments like facility management, HR, marketing, or finance. They process tickets and support internal or external customers.
Customer Users are the end-users who submit and track requests via OTOBO. This group includes employees who contact the IT help desk as “internal customers,” as well as external end customers or service providers who interact with OTOBO through the self-service portal.
OTOBO supports local management of agents and customer users, as well as integration with external source systems like Active Directory, LDAP, or databases.
Groups: Efficient User Permissions
Groups in OTOBO combine users who should have the same permissions, such as access to specific queues (work areas). By assigning a group to one or more queues, you can assign a set of exclusive permissions to that group.
For example, if agents need permission to access Configuration Items (CIs) within the OTOBO CMDB, they must be assigned to the “itsm-configitem” group. Additional settings are required if customer users should also be able to view CIs through the self-service portal.
One-to-One Group-Queue Assignment
In OTOBO, each queue can be assigned to exactly one group (e.g., 2nd Level Support). The group enables precise control over permissions and allows specific activities within the queue.
Many-to-Many Agent-Group Assignment
By assigning agents to a group, they inherit the permissions associated with that group. Depending on how granular the permission concept is and whether roles are used, group members can also have individual permissions within the group and the assigned queue.
The advantage of this approach is efficiency and security. By assigning an agent to a group, you can quickly grant them access to the entire work area. Conversely, you can deactivate a user’s access to multiple queues by removing their group assignment with a single click, without having to laboriously remove each permission individually.
For a detailed overview of the group concept and agent-group assignment, refer to the official OTOBO documentation.
Roles: Saving Time and Bundling Permissions
The role concept bundles role-specific permissions that employees need to perform their tasks in specific responsibility areas (queues). It also provides an additional abstraction layer above groups.
Many-to-Many Role-Group Assignment
When assigning roles to one or more groups, the permissions associated with the group(s) are linked to the role. With a role, you can assign the permissions of multiple groups in a single step.
Roles simplify permission management for individual users with comprehensive permissions, increasing efficiency when onboarding or offboarding employees. Instead of setting each user’s permissions individually through group assignments, you can assign a pre-defined role with a single click, which already includes the group assignments – a task completed.
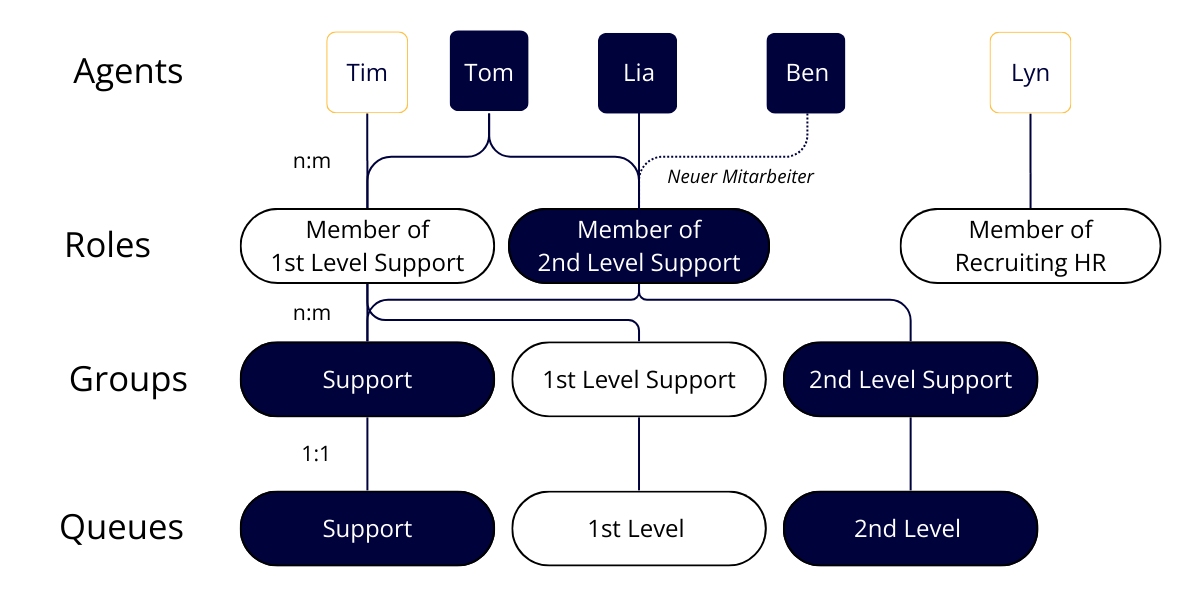
Figure: OTOBO Permission Concept with Roles
A new OTOBO installation doesn’t come with any predefined roles. For a detailed overview of the role concept and setup instructions, check out the official OTOBO documentation.
Permissions – Editing Tickets and Controlling Data Access
Now that we’ve assigned agents or roles to one or more groups, it’s time to define the specific activities that users (agents or customer users) can perform in each queue.
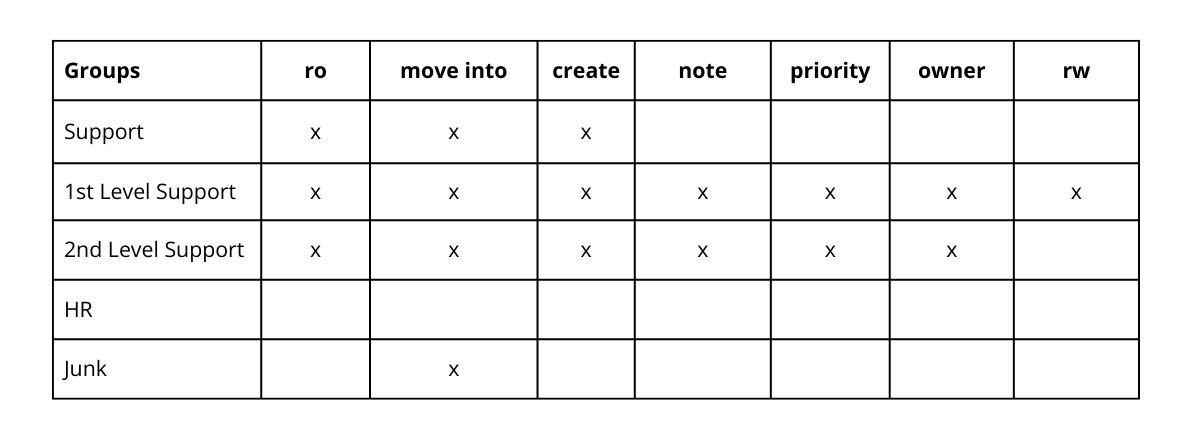
Figure: Example of a Role Configuration (1st Level Support) with Groups and Permissions
These can include the standard permissions that come with OTOBO, such as creating tickets, moving them, adding and reading internal notes, changing priority, assigning owners, and controlling access levels (e.g., read-only or full read-write access).
Additional permissions can be added through the system configuration settings.
In conclusion, OTOBO makes it easy to implement even complex permission concepts in a secure and efficient way.
To successfully set up permission management, you need to have a clear understanding of your current and future requirements for work areas and responsibilities. It’s essential to consider these needs when selecting a service management solution to ensure the solution can scale with your organization in the future.
OTOBO supports organizations of all sizes in achieving their security and data protection goals, whether they manage permissions locally or import them from third-party systems. The flexibility of OTOBO’s permission management makes it easy to administer permissions, protecting sensitive data, complying with data protection policies, and enabling users to work efficiently.
Company
OTOBO | Simplify work and create exceptional service experiences.
The Source Code Owner and Maintainer of OTOBO.
Software
Service Management Platform
OTOBO Demo
OTOBO Download
OTOBO Documentation
Report a security issues:
security@otobo.org